Recently, web3 phishing websites have resulted in significant user losses. These phishing websites disguise themselves as reputable projects and deceive users into signing transactions that rapidly deplete their crypto assets. Meanwhile, a new form of scam-as-a-service (SaaS) has emerged. Specifically, the service provider supplies collaborators with the phishing toolkit and requires a percentage, typically 20% or 30%, of their earnings in return. Among these service providers, a notorious case is “Inferno Drainer,” which has inflicted millions of dollars in losses upon thousands of victims. In this blog, we take “Inferno Drainer” as an illustrative example to analyze the profit-sharing process.
The Operational Process of Inferno Drainer
In general, the operational process of Inferno Drainer can be divided into five steps.
- The provider of “Inferno Drainer” advertises their official promotion channel in TG, discord, and twitter.
- A collaborator, who seeks to monetize his/her traffic but lacks technical expertise, joins the channel and shares his/her account with the provider.
- The provider supplies the collaborator with a ready-to-go phishing toolkit and deployment instructions.
- The collaborator launches the phishing website.
- When a victim falls for the scam, his/her crypto assets are usually transferred to a designated phishing account. Subsequently, the profits are shared between the Drainer admin and the collaborator account.
In the following paragraphs, we will reveal the profit-sharing process by analyzing two phishing scenarios involving ETH and ERC20, respectively.
ETH Phishing Scenario
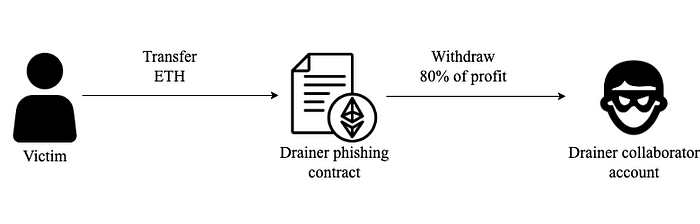
The above diagram illustrates the profit-sharing process in ETH phishing. To deceive users of their ETH, the scammer deploys a phishing contract containing a payable function such as ‘mint’ or ‘airdrop’. Enticed by these function names, the victim mistakenly signs the phishing transaction. Upon receiving the victim’s ETH, the admin swiftly invokes the withdraw function, transferring 80% of the funds to the collaborator account. The remaining 20% is retained within the contract and will be withdrawn at the appropriate time.
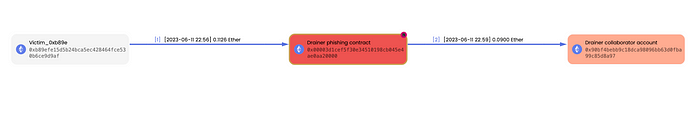
Here is a genuine case depicted with MetaSleuth. Victim_0xb89e unintentionally sent 0.1126 ETH to the phishing contract. Subsequently, 80% of this amount, equivalent to 0.09 ETH, was rapidly withdrawn and transferred to a collaborator account.
You can review the fund flow using the following link: https://metasleuth.io/result/eth/0xfa59f0531af65c0a16b6c1834e3921e7fa519734d4d90675e479e99722d6f4ba?source=71470e57-cb33-45b9-a264-76e374b95765.
ERC20 Token Phishing Scenario
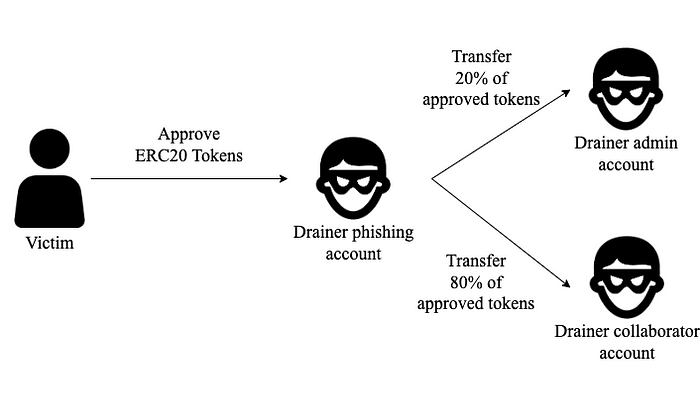
This diagram illustrates the profit-sharing process in ERC20 token phishing. Unlike ETH phishing, in this case, the phishing account is an EOA (Externally Owned Account). The phishing website initially prompts the victim to approve their ERC20 tokens to the phishing account. Subsequently, the phishing account transfers 20% of the approved tokens to the admin account, while the remaining 80% are transferred to the collaborator account.
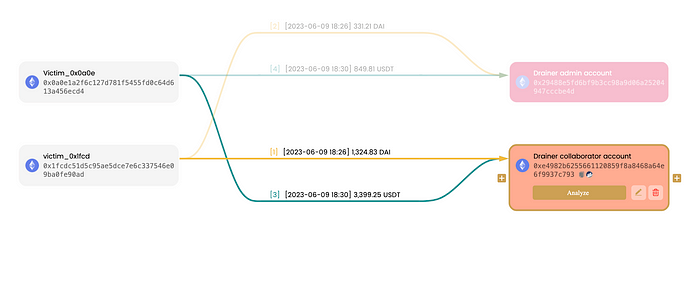
Here is a concrete case. `Victim_0x0a0e` and `Victim_0x1fcd` unintentionally approved their USDT and DAI to the phishing account. Subsequently, the phishing account transferred 20% and 80% of these tokens to the admin and collaborator accounts, respectively.
You can review the fund flow using the following link: https://metasleuth.io/result/eth/0x1ba31a2751259048e1e559df59bcdf80015e15359674aaf64e936cb98630b810?source=d0a430bd-2b7e-46bb-8788-b0f8ba39f366.
Our discoveries
To gather evidence of profit-sharing activities, we have conducted a comprehensive analysis of all history transactions associated with the admin account. It is important to highlight that we solely focus on cases where the profit-sharing percentage is either 20% or 30%. In our investigation, we discovered 3,223 profit-sharing transactions totaling $5.02 million in funds. Among these transactions, the admin account has received $1.07 million as fees from 351 collaborators. Additionally, our phishing detection system has identified 574 related phishing websites.
To protect users from Inferno Drainer, we have promptly reported all of these websites to MetaMask (https://github.com/blocksecscamreport/eth-phishing-detect/commits?author=blocksecscamreport&before=01bf4f680061bc39ecd2d55425774fc3092aa3cc+35).
Summary
This particular form of SaaS, involving profit-sharing, is rapidly evolving. We will remain vigilant, continually monitoring related phishing accounts and transactions. We urge users to exercise caution and diligently review transaction details before approving any actions. This blog aims to help users understand the profit-sharing process and protect themselves against potential phishing websites in the blockchain domain.
About MetaSleuth
MetaSleuth is a crypto funds visualization and analysis tool developed by BlockSec. It allows users to investigate and share findings and clues about fund transfers. CEX, wallets, and VASP can use it to build their compliance services.
Twitter: https://twitter.com/MetaSleuth
Website: https://metasleuth.io
