
We find there exist two serious logic vulnerabilities in the @AkuDreams contracts(https://etherscan.io/address/0xf42c318dbfbaab0eee040279c6a2588fa01a961d). The first vulnerability can cause a DoS attack and the second vulnerability will make the project fund (more than 34M USD) being locked forever.
Vulnerability I

The first vulnerability exists in the processRefunds function. This function has a loop that will refund each bid user's fund. However, the bidder can be a malicious contract that reverts the transaction. This can cause the invocation of processRefunds revert, and none of user's refunds can be successful. Fortunately, this vulnerability has not been exploited.
We suggest that the contract can take the following measures to refund users.
- Ensure that only EOA can bid
- Use ERC20 token, e.g., WETH, instead of ETH
- Has function that allows a user to get the refund by himself
Vulnerability II
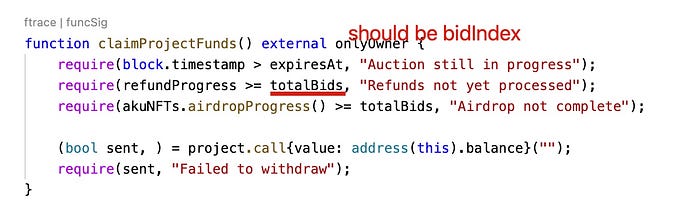
The second vulnerability is a software bug. In the claimProjectFunds function, the project owner can claim the Ether in the contract. However, the require statement require(refundProgress >= totalBids, "Refunds not yet processed"); has a bug, which should compares the refundProgress with _bidIndex instead of totalBids. Due to this vulnerability, the requirement will never be satisfied, and the Ether (11,539.5 Ether) in the contract can be locked for ever.
Summary
We are surprised again (after the NBA NFT case yesterday) that how a high-profile project can neglect the basic software security practice. At least, the project should write enough test cases. Unfortunately, we suspect that the projects are too busy to write the test cases, and lose 34M USD forever.
About BlockSec
The BlockSec Team focuses on the security of the blockchain ecosystem, and collaborates with leading DeFi projects to secure their products. The team is founded by top-notch security researchers and experienced experts from both academia and industry. They have published multiple blockchain security papers in prestigious conferences, reported several zero-day attacks of DeFi applications, and released detailed analysis reports of high-impact security incidents.
- Twitter: [BlockSecTeam]| [BlockSecAlert]
- Medium: https://blocksecteam.medium.com
- Website: https://www.blocksecteam.com
