By BlockSec
On September 16th, 2022, we detected that some attackers successfully harvested lots of ETHW by replaying the message (i.e., the calldata) of the PoS chain on EthereumPoW (aka the PoW chain). The root cause of the exploitation is that the Omni bridge on the PoW chain uses the old chainId and doesn’t correctly verify the actual chainId of the cross-chain message.
We immediately contacted the official team of EthereumPoW. The team was actively willing to take actions, and they also tried to communicate with the Omni Bridge.

However, as more and more attacks were observed in the wild, we believed that the risk should be notified to the public, and we published the alert on September 18th, 2022.
As there still exists some misunderstanding about these attacks, i.e., replaying the transaction rather than the message. In this report, we’d like to provide a detailed analysis to clarify it.
Attack Analysis
Here is an example of exploitation transactions:
- PoS Tx on Ethereum: https://etherscan.io/tx/0xbddb0cc8bc9949321e1748f03503ed1a20dd618fbf0a51dc5734c975b1f8bdf5
- (Exploitation) PoW Tx on EthereumPow: https://www.oklink.com/en/ethw/tx/0x9c072551861ce384203516f4d705176a2d2e262d5b571d853467425f1a861fb4
Note that, these two transactions are different, however, the calldata (or input data) of these two transactions are exactly the same:
0x23caab4900000000000000000000000000000000000000000000000000000000000000400000000000000000000000000000000000000000000000000000000000000180000000000000000000000000000000000000000000000000000000000000011500050000a7823d6f1e31569f51861e345b30c6bebf70ebe7000000000000e0f6f6a78083ca3e2a662d6dd1703c939c8ace2e268d88ad09518695c6c3712ac10a214be5109a655671000927c00101806401867f7a4d000000000000000000000000c02aaa39b223fe8d0a0e5c4f27ead9083c756cc2000000000000000000000000a6439ca0fcba1d0f80df0be6a17220fed9c9038a00000000000000000000000000000000000000000000000ad78ebc5ac62000000000000000000000000000000000000000000000000000000000000000000080000000000000000000000000000000000000000000000000000000000000001482faed2da812d2e5cced3c12b3baeb1a522dc67700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000105041c1b1c1c981df6cdaf073d55b78d7f0c7e2b421a569bff677a9464d1d5203672d7b5a3d6af658d14ebc11c26f2547fd0aed01750cca58753a0a79b297bad8a62a71eb6b7ac2099611604eff316e7fe733e9981c1b3890cb04ff9d43612e6f2687227f0226cfa27e4b6cd96a10865e04aa9e0f369dda7548771a094f69bf0a9fa6c27257e22d2b1bbb84beb52ad3966592037b328d352fce375a1fa75cb3fbfd18166f4177a19ad2cc74ce67da68f5ce17b857e6382c3ebf20f76482534135f426f4a74222daa07d9f401cb8baca4339ecd44e285df0e0cb88447a31d08b673cecc67d22c7e6e0ce5afd2ac9439c5a8b68f05077b850cdfdfb79cdaefc5b103bb69360944000000000000000000000000000000000000000000000000000000It is just the input data of invoking of the safeExecuteSignaturesWithAutoGasLimit function.
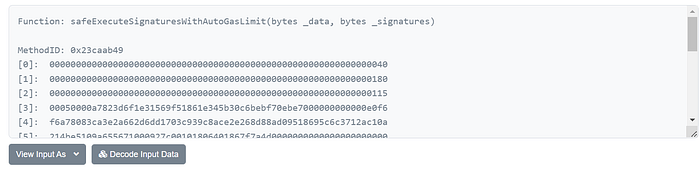
Obviously, the attacker (0x82fae) first transferred 200 WETH through the omni bridge of the Gnosis chain, and then replayed the same message on the PoW chain and got extra 200 ETHW. By doing so, the balance of the bridge contract deployed on the PoW chain could be drained.
Vulnerability Analysis
After anaylzing the source code of the Omni bridge, we find that there DOES exist the logic to verify the chainId.
function _isDestinationChainIdValid(uint256 _chainId) internal returns (bool res) {
return _chainId == sourceChainId();
}Unfortunately, the verfied chainId used in this contract comes from the value stored in the storage named unitStorage:
/**
* Internal function for retrieving chain id for the source network
* @return chain id for the current network
*/
function sourceChainId() public view returns (uint256) {
return uintStorage[SOURCE_CHAIN_ID];
}It is NOT the actual chainId fetched through the CHAINID opcode, which was proposed in EIP-1344. This is probably due to the fact that the code is quite old (using Solidity 0.4.24). The code works fine all the time until the fork of the PoW chain.
In short, the root cause of the exploitation is that the Omni bridge on the PoW chain uses the old chainId and doesn’t correctly verify the actual chainId of the cross-chain message. Besides, the similar issues may exist in other protocols.
The Impact
The straightfoward impact is that the attacker(s) could harvest lots of ETHW (and also other tokens owned by the bridge on the PoW chain) and traded them in some marketplaces (e.g., some CEXs). By doing so, the price of ETHW might be affected due to the increase of the liquidity. Hence users/investors should be cautious about the trade of these tokens on the PoW chain.
Conclusion
Solidity developers should pay special attention when dealing with the chainId that is designed to be maintained by the contract itself.
About BlockSec
The BlockSec is dedicated to building blockchain security infrastructure. The team is founded by top-notch security researchers and experienced experts from both academia and industry. We have published multiple blockchain security papers in prestigious conferences, reported several zero-day attacks of DeFi applications, and successfully protected digital assets that are worth more than 5 million dollars by blocking multiple attacks.
- Twitter: [BlockSecTeam]
- Medium: https://blocksecteam.medium.com
- Website: https://www.blocksec.com
